This report is an Access Now publication. We would like to thank Access Now’s Digital Security Helpline for conducting the forensic investigation as well as other Access Now team members who provided support, including Méabh Maguire, Alexia Skok, Sage Cheng, Donna Wentworth, Peter Micek, Natalia Krapiva, Rand Hammoud, Thomas Kaye, and Milica Pandzic. We would also like to thank the partners who have been involved at various points in this investigation, including the Citizen Lab at the Munk School of Global Affairs at the University of Toronto, Human Rights Watch, Amnesty International’s Security Lab, the Organized Crime and Corruption Reporting Project (OCCRP), and our local partners in Jordan.
Table of contents
- Introduction
- The investigation
- The story so far
- Who was hacked?
- How were they hacked?
- Increased use of spyware amid escalating crackdown on civil society
- Call to action
Introduction
A joint forensic investigation by Access Now, the Citizen Lab at the Munk School of Global Affairs at the University of Toronto (the Citizen Lab), and local partners has uncovered that at least 35 individuals in Jordan have been targeted with Israeli firm NSO Group’s Pegasus spyware.
Amid escalating repression and a crackdown on civic space, press freedoms, and political participation in Jordan, our investigation reveals staggeringly widespread use of Pegasus to hack and spy on the country’s journalists, political activists, civil society actors, and human rights lawyers.
The investigation
Access Now and the Citizen Lab’s joint forensic investigation found traces of Pegasus spyware on the mobile devices of 30 activists, journalists, lawyers, and civil society members. Further work by Human Rights Watch (HRW), Amnesty International’s Security Lab, and the Organized Crime and Corruption Reporting Project (OCCRP) identified five more Pegasus victims, bringing the total number of Pegasus targets in Jordan uncovered in this investigation to 35 individuals. One of these victims had been previously targeted with Pegasus on other occasions. We believe this is just the tip of the iceberg when it comes to the use of Pegasus spyware in Jordan, and that the true number of victims is likely much higher.
The story so far
The first publicly confirmed case of Pegasus being used in Jordan occurred in March 2021, with the hacking of Jordanian human rights lawyer Hala Ahed, revealed in January 2022 by Access Now and Front Line Defenders. In April 2022, the Citizen Lab and Front Line Defenders found that four more human rights defenders and journalists had also been targeted with Pegasus, including Malik Abu Orabi, Ahmed Neimat, and two other women journalists.
Subsequent threat notifications sent by Apple, most recently in October 2023, led a number of people in Jordan to ask the Citizen Lab and Access Now’s Digital Security Helpline to check their mobile devices for spyware.
Who was hacked?
Our investigation unveils the widespread hacking of NGO representatives, activists, journalists, and human rights lawyers in Jordan using Pegasus spyware. The attacks encompassed in our investigation span from 2019 until September 2023, with some victims reinfected with Pegasus multiple times — demonstrating the relentless nature of this targeted surveillance campaign. For example, we found that Hala Ahed was targeted once again. Given the risk of reprisals, some victims wished to remain anonymous. Detailed information on the 13 victims who consented to being identified publicly is presented below.
| NGO representatives 4 | Activists 5 |
| Human rights lawyers 8 | Politicians 1 |
| Journalists and media organizations staff 16 | Information technologists 1 |
NGO representatives
// Human Rights Watch
Amnesty Tech and HRW found that personal mobile devices belonging to two of HRW’s Jordan-based staff were targeted with Pegasus spyware. On October 2, 2022, Adam Coogle, a deputy director with HRW’s Middle East and North Africa division, was hacked with Pegasus spyware through a zero-click attack (A zero-click cyberattack uses existing vulnerabilities in an operating system to potentially compromise a device without any action from its owner). The attack occurred exactly two weeks after HRW published a damning report on increasing government repression in Jordan.
Hiba Zayadin, HRW’s senior researcher for Jordan and Syria, was also targeted with Pegasus. On August 29, 2023, both Coogle and Zayadin received threat notifications from Apple warning them that state-sponsored attackers had attempted to compromise their personal mobile devices remotely. However, HRW found no evidence of further attacks being successful.
// Manal Kasht
Manal Kasht is another civil society activist targeted with Pegasus spyware. Kasht is a Jordanian translator and founder of Shabbat, a civil society organization aimed at empowering women in politics.
Human rights lawyers
// Omar Atout
Omar Atout is a Jordanian lawyer, constitutional expert, and political activist. He is outspoken on issues related to Jordan and Palestine on social media, and writes about Jordan’s reform initiatives in the media. He is also a co-founding member of the Arab Association of Constitutional Law and a member of the Jordan Bar Association. Forensic investigation by Access Now’s Digital Security Helpline and the Citizen Lab found that Atout’s mobile device was compromised by Pegasus on or around December 11, 2022. According to Atout, he received multiple notifications from Apple that state-sponsored attackers attempted to compromise his iPhone.
// The National Forum for the Defense of Freedoms
Five members of the National Forum for the Defense of Freedoms — a group of human rights lawyers providing pro bono support to prisoners of conscience, labor unions, and political parties in Jordan — were also targeted with Pegasus spyware. The Forum has provided legal aid for a number of political prisoners, journalists, and citizens in Jordan detained for protesting or expressing their opinions online. The five members targeted were:
Hala Ahed
Hala Ahed is an award-winning Jordanian human rights lawyer who works with human rights organizations to defend women’s rights, workers’ rights, and freedoms of opinion, expression, and peaceful assembly in Jordan. She defends prisoners of conscience and labor unions in Jordan, and is a member of the legal team defending the Jordan Teachers’ Syndicate, one of Jordan’s largest labor unions, which the Jordanian government forcibly dissolved in 2020. Our investigation found that Ahed’s device was targeted with Pegasus spyware for a second time on or around February 20, 2023, following a previous successful hack that occurred on March 16, 2021. The hacking attempt occurred amidst a broader campaign of harassment against her. In June 2023, after a Jordanian nonprofit organization announced that Ahed will facilitate an online workshop series on feminism, she was subject to a vicious torrent of online attacks and smear campaigns on social media, even receiving death threats.
Alaa Al-Hiyari
Alaa Al-Hiyari is a Jordanian lawyer, political activist, member of the National Forum for the Defense of Freedoms, a member of the freedom committee of Jordan’s Bar Association, and also a member of the Partnership and Salvation political party. According to the Citizen Lab’s forensic analysis, Al-Hiyari’s mobile device was infected with Pegasus on or around January 2, 2023.
Jamal Jeet
Jamal Jeet is a human rights lawyer and member of the National Forum for the Defense of Freedoms. In our investigation, the Citizen Lab identified a suspicious domain linked to Pegasus spyware in one of Jeet’s SMS messages, received on his Android mobile device on March 26, 2020. However, we were unable to definitively ascertain whether the hacking attempt was successful or not. On January 12, 2023, Jeet was detained by the Jordanian authorities, then released on bail, for writing two Facebook posts; one criticizing the Wadi Araba peace treaty signed between Israel and Jordan in 1994, and another expressing support for truck drivers’ strikes and protests over fuel prices, held in the southern city of Ma’an in December 2022.
Asem Al-Omari
Asem Al-Omari is a Jordanian human rights lawyer and member of the National Forum for the Defense of Freedoms. On March 12, 2020, Al-Omari received an SMS message on his Android phone, containing a suspicious domain linked to Pegasus spyware. We could not ascertain whether or not the hacking attempt was successful.
Loay Obeidat
Loay Obeidat is a Jordanian lawyer, former judge, and member of the National Forum for the Defense of Freedoms. The Citizen Lab’s forensic analysis found that Obeidat’s iPhone was hacked with Pegasus spyware three times, on or around August 12, 2022 and then on or around April 25 and June 11, 2023. Prior to that, his mobile device was targeted twice around mid-March 2023, but there were no indicators of successful infection.
Journalists and media organizations
Journalists in Jordan are a primary target for unlawful surveillance and constitute most of the spyware victims identified in this investigation. We discovered that at least 16 individuals working either as journalists or for independent media organizations in Jordan were hacked with Pegasus between 2020 and 2023.
// Organized Crime and Corruption Reporting Project (OCCRP)
Two of OCCRP’s journalists in Jordan were found to have been targeted multiple times with Pegasus spyware. According to OCCRP and Amnesty International’s Security Lab’s forensic analysis, Rana Sabbagh, senior editor for the Middle East and North Africa (MENA) at OCCRP and co-founder of the award-winning Arab Reporters for Investigative Journalism (ARIJ), had both of her phones targeted with Pegasus spyware. OCCRP found evidence of targeting throughout February and April 2021.
Lara Dihmis, a MENA investigative reporter with OCCRP, was also hacked with Pegasus on June 18, 2022. Both have worked on local and regional components of several global cross-border investigations into corruption, shadowy financial systems, and offshore companies.
// Daoud Kuttab
Daoud Kuttab is an award-winning Palestinian-American journalist, media activist, and columnist based in Jordan. He was a Ferris Professor of Journalism at Princeton University and is currently director-general of Community Media Network, a nonprofit organization overseeing cultural and media projects including community radio station Radio Al-Balad, and the network’s website, AmmanNet.Net.
Between February 2022 and September 2023, Kuttab was hacked with Pegasus spyware three times — on or around February 21 and June 17, 2022, and again on or around September 3, 2023. On March 8, 2022, two weeks after the first hacking incident, Kuttab was arrested upon arrival at Queen Alia International Airport outside of Amman. He was detained under the Cybercrime Law for an article written in 2019, before being released a few hours later on bail.
The Citizen Lab’s forensic analysis also uncovered seven other attempts to infect Kuttab’s mobile device with Pegasus between April and August 2023. One of these was a sophisticated social engineering attack launched in July 2023, where the attacker impersonated a journalist from media outlet The Cradle inquiring about Jordan’s new cybercrime law while sending several malicious links.
// Hosam Gharaibeh
Hosam Gharaibeh is the director of Husna Radio and presenter of its morning show. The Citizen Lab found that his device was successfully infected nine times between March and August 2020, between March and April 2021, and later again on or around November 20, 2022. There were also three failed attempts to infect his device in December 2022 and January 2023.
How were they hacked?
The Pegasus victims we uncovered were targeted with both zero-click and one-click attacks. The malware forensic analysis conducted by Access Now and the Citizen Lab revealed instances of threat actors employing the NSO Group zero-click exploits “PWNYOURHOME,” “FINDMYPWN,” “FORCEDENTRY,” and “BLASTPASS” to deliver Pegasus spyware.
We also observed sophisticated social engineering attacks delivering malicious links to victims via WhatsApp and SMS. In some cases, perpetrators posed as journalists, seeking a media interview or a quote from targeted victims, while embedding malicious links to Pegasus spyware amid and in between their messages.
In one instance, one victim received a WhatsApp message from someone claiming to be a journalist working for media outlet The Cradle, who approached the victim requesting a quote on Jordan’s new cybercrime law and its impact on freedoms in the country.
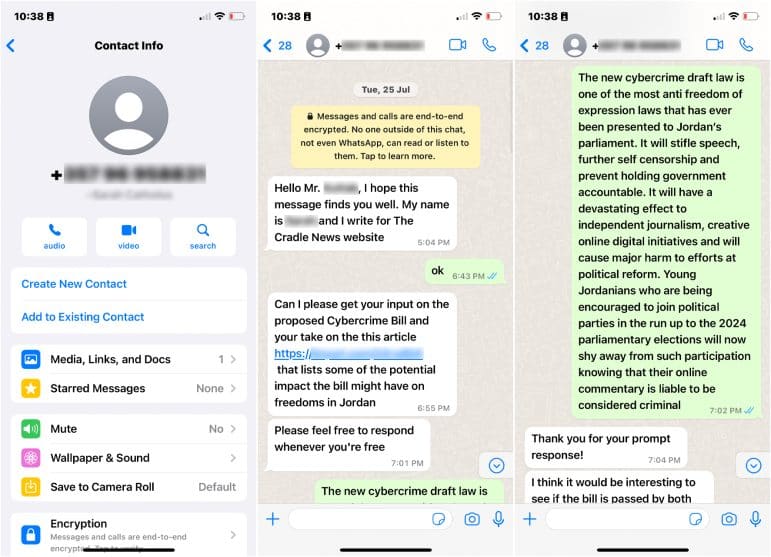
Figure 1: Screenshots of the social engineering attack impersonating media outlet The Cradle

Figure 2: Screenshots of the social engineering attack impersonating media outlet The Cradle

Figure 3: Screenshots of the social engineering attack impersonating media outlet The Cradle
As mentioned earlier, many victims were reinfected with Pegasus multiple times, including during our investigation period. We also observed that activating Lockdown Mode for the iPhone appears to have blocked some attempts to compromise Apple devices with Pegasus.
Increased use of spyware amid escalating crackdown on civil society
Over the past four years, Jordanian authorities have dialed up their repression of citizens’ rights to freedom to expression, association, and peaceful assembly. In 2021, Civicus downgraded its rating of Jordan’s civic space from “obstructed” to “repressed,” while Freedom House rated Jordan as “Not Free” in its Global Freedom Report and “Partly Free” in its 2023 Freedom on the Net Report.
Journalists, human rights defenders, labor unions, and activists from the Hirak — a social justice protest movement advocating for human rights and reforms — are routinely harassed, detained, and prosecuted under vague, wide-reaching, and repressive laws, including Jordan’s 1960 Penal Code, 2006 Anti-Terrorism Law, and 2015 Cybercrime Law. Between March and April 2022, for instance, authorities arrested hundreds of journalists, politicians, and activists under vague stipulations within the Penal Code, the Cybercrime Law, and the abusive Crime Prevention Law, aiming to silence anti-government criticism, dissent, and planned protests. At least 12 detainees were charged with “spreading false news” and “inciting strife.” In the same period, at least six journalists, including Daoud Kuttab, were also detained and interrogated over their social media posts or journalistic work.
In late 2022 and early 2023, several lawyers and activists were arrested in connection to protests over rising fuel prices in south of Jordan. Some of those arrested include spyware victim Jamal Jeet. In December 2022, authorities banned TikTok under the pretext of the platform being misused, and for “inciting violence and chaos” during the protests.
In August 2023, Jordan’s authorities replaced the 2015 Cybercrime Law with a draconian new cybercrime law, criminalizing online speech via vague terminology such as spreading “fake news,” “promoting, instigating, aiding, or inciting immorality,” “online assassination of personality,” “provoking strife,” and “undermining national unity.” Authorities have routinely disrupted internet access, particularly during mass protests, including throttling internet services during 2018 and 2019 anti-austerity protests, 2020 teachers union protests, 2021 COVID-19 protests triggered by the Al-Salt hospital incident, and December 2022 truck drivers’ protests.
Jordanian authorities have also dissolved political parties and labor unions in retaliation for protests or opposition to state policies. For example, the Partnership and Salvation party has faced ongoing state intimidation and persecution since its inception in 2018. In 2020, authorities dissolved the Jordanian Teachers Syndicate (JTS), Jordan’s largest union, and arrested its board members in retaliation for a one month-long teachers’ strike in 2019 and ensuing mass protests. The authorities also issued a gag order preventing the media from covering the case, and arrested around 1,000 teachers protesting the union’s dissolution.
Many of the Pegasus victims identified through our investigation either worked on or covered the teachers’ strike, the detention and incarceration of teachers, and the forced closure of the teachers’ union. Some of the targeted journalists also covered highly sensitive political affairs, or were involved in media investigations such as the Panama Papers, Pandora Papers, and the Suisse Secrets leaks, while some of the victims are Palestinian activists based in Jordan, who lead public campaigns denouncing the Israeli occupation and the normalization deal with Jordan.
Call to action
Surveillance technologies and cyberweapons such as NSO Group’s Pegasus spyware are used to target human rights defenders and journalists, to intimidate and dissuade them from their work, to infiltrate their networks, and to gather information for use against other targets. The targeted surveillance of individuals violates their right to privacy, freedom of expression, association, and peaceful assembly. It also creates a chilling effect, forcing individuals to self-censor and cease their activism or journalistic work, for fear of reprisal.
Our investigation into the widespread use of Pegasus spyware in Jordan once again demonstrates how NSO Group enables state repression and facilitates human rights abuses around the world. There have been some positive steps toward holding spyware companies accountable. Israeli spyware firms NSO Group and Candiru were added to the U.S. Department of Commerce’s Entity List in 2021, with four other Intellexa entities joining them in July 2023. U.S. President Biden has banned the operational use of certain commercial spyware by federal government agencies, while both Meta and Apple have brought lawsuits against NSO Group. Despite these efforts, however, there is little evidence that the spyware industry is exercising any restraint, while NSO Group shows no sign of ending the rights-abusing commercial activities it profits from.
In this light, we urge Jordan’s government to:
- Ensure prompt, impartial, and independent investigation into hacking allegations, and establish accountability and remedy mechanisms for surveillance victims;
- Uphold its Constitution and its human rights obligations under the International Covenant for Civil and Political Rights (ICCPR), which it has signed and ratified, to protect the rights to freedom of expression, peaceful assembly, and association; and
- Cease the intimidation, harassment, detention, censorship, surveillance, and prosecution of civil society representatives and organizations, and revoke or amend its draconian laws enabling this repression.
We urge all world governments, including Jordan’s, to:
- Halt the use of Pegasus spyware, and implement an immediate moratorium on the export, sale, transfer, servicing, and use of targeted digital surveillance technologies, until rigorous human rights safeguards are put in place to regulate such practices;
- Where there is evidence that commercial spyware technology facilitates or enables human rights abuses, implement a ban on said technology and its vendors;
- Reaffirm protections for all journalists and media workers, and safeguard press freedom, by recognizing that journalists and media workers are not legitimate surveillance targets simply by virtue of doing their jobs;
- Hold the companies developing and distributing targeted surveillance technologies, and their investors, accountable for their failure to respect human rights and for the role they play in enabling abusive end uses, and demand transparency from said companies around their clients and practices, in particular regarding data collection and processing practices;
- Impose sanctions on NSO Group, its staff, third-party resellers, and on the sale and transfer of their spyware technologies that threaten human rights, media freedom, peace, and security; and
- Establish accountability mechanisms for surveillance victims to access remedy and protection.
